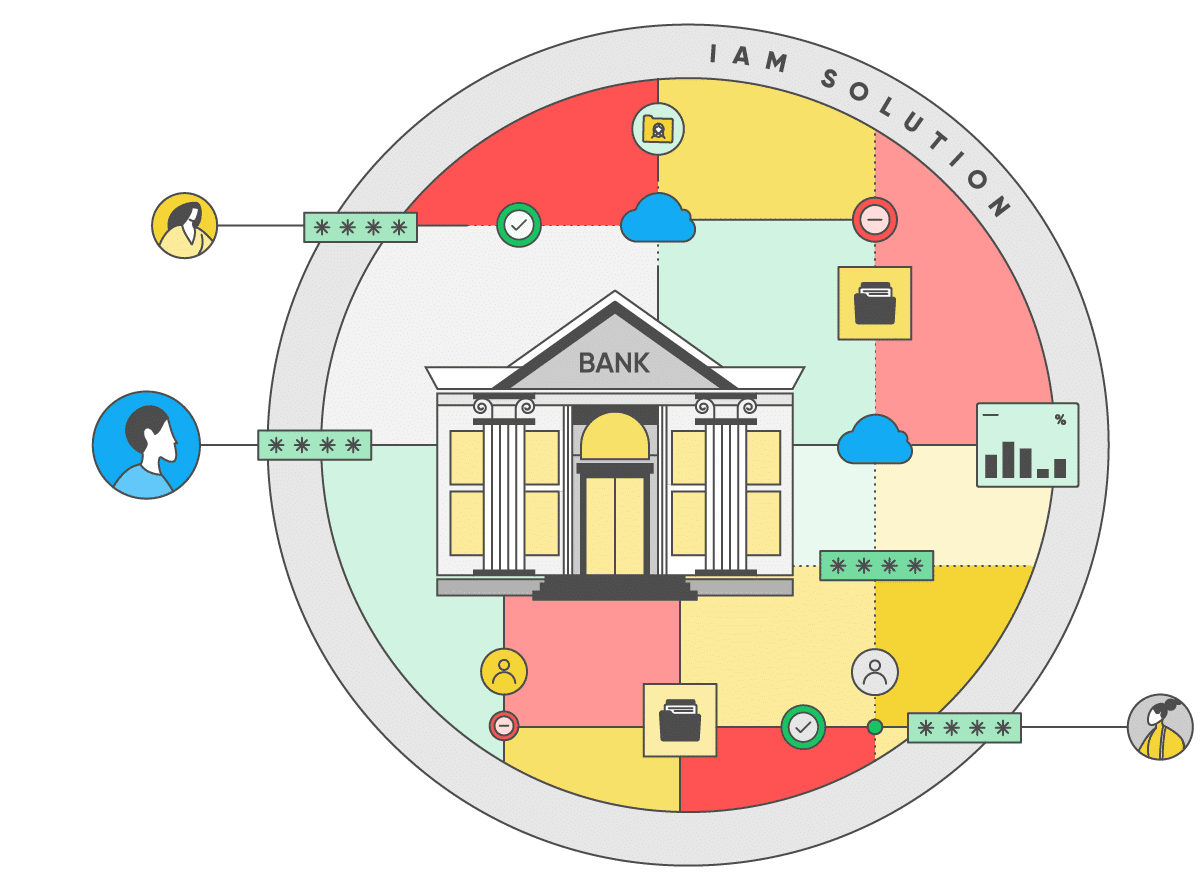
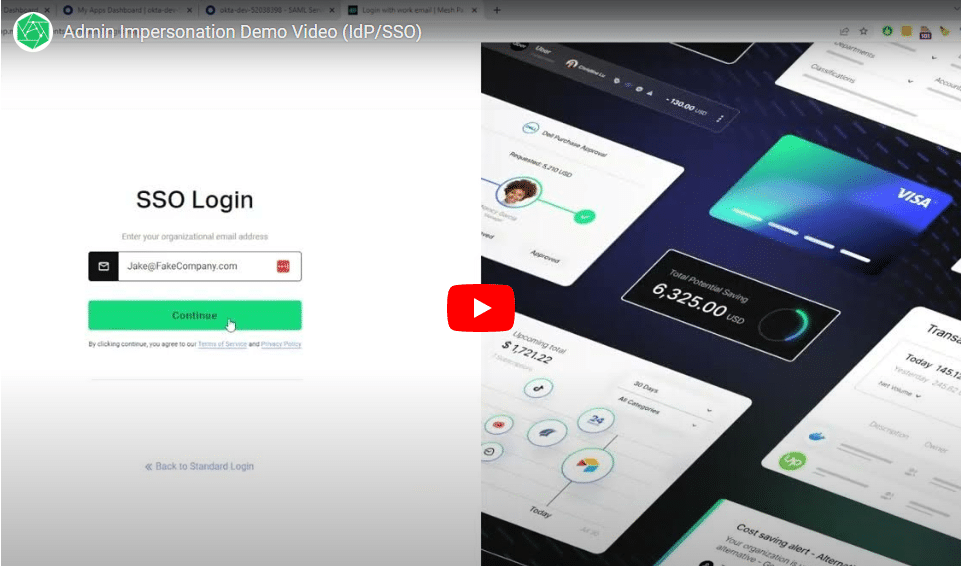
Ensure the integrity and security of your Cloud IAM to protect your entire cloud environment from identity-based attacks.
- Continuously monitor your IAM layer for active threats including account takeover, user impersonation, and persistent threats
- Detect and address misconfigurations and dangerous trust relationships in your IAM infrastructure
- Detect and remediate weak authentication controls and Multi-Factor Authentication (MFA) bypass