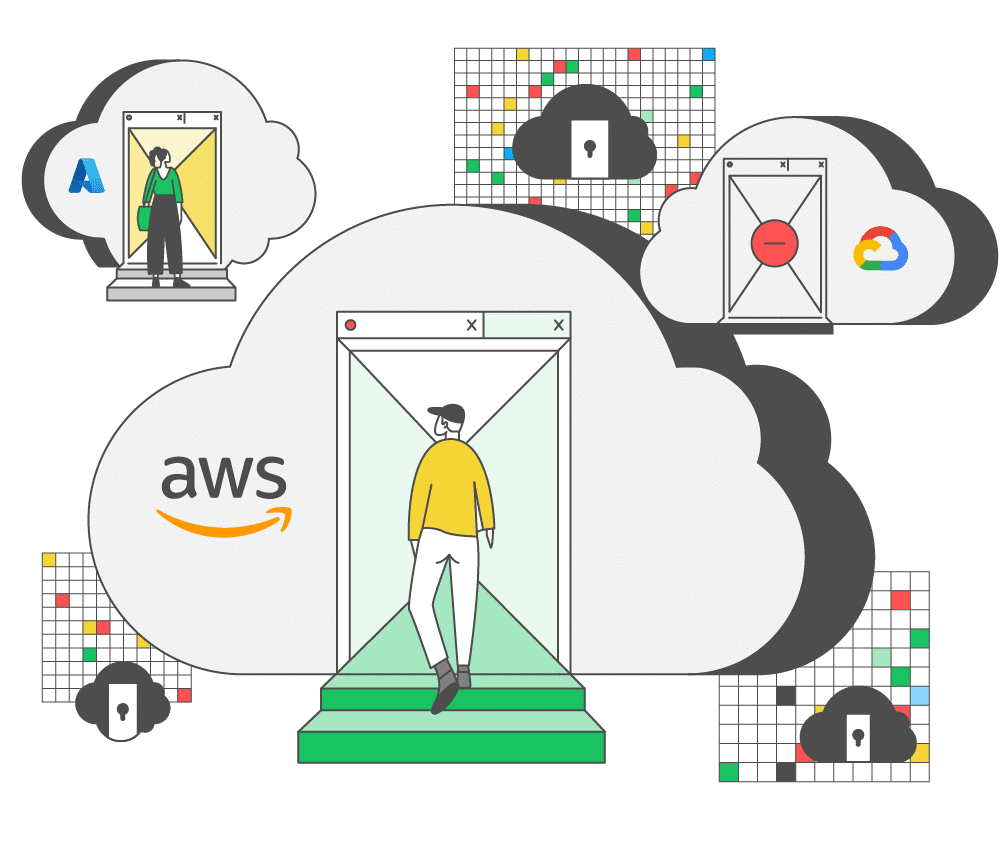
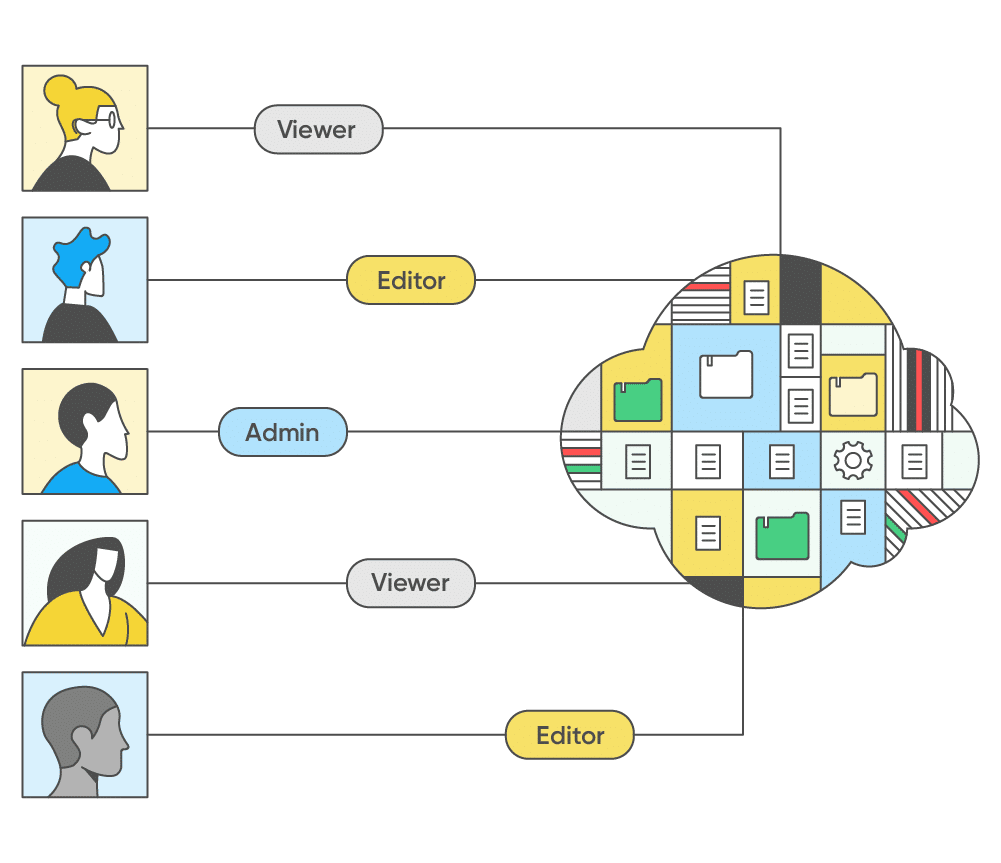
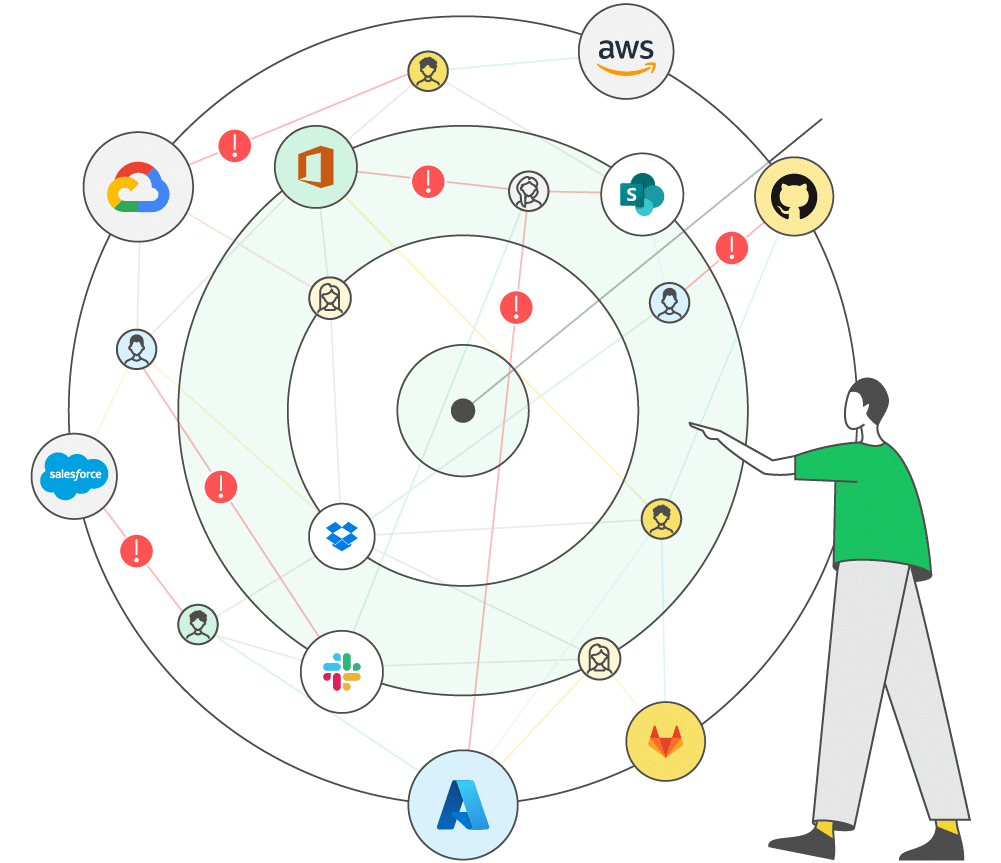
Mitigate complex access risks from human and machine identities, including 3rd-parties, across your cloud infrastructure, applications, and IAM solutions.
- Eliminate stale access across your entire cloud environment
- Detect and eliminate over-privileges based on granular usage data and AI-based recommendations
- Identify and mitigate privilege escalation paths across IAM and cloud entitlements