3 Lessons Learned from Attacks on Okta Super Admins
Discover the latest Okta security incident, learn about identity federation abuse, and find out how to protect your Okta environment. Explore the risks and solutions.

Discover the latest Okta security incident, learn about identity federation abuse, and find out how to protect your Okta environment. Explore the risks and solutions.
Explore Authomize’s new open source training tool designed to raise awareness and enhance resilience against MFA Bombing attacks.
Authomize’s Security Research Lab has released a new report outlining misconfiguration risks for Okta users that can lead to the theft of cleartext Okta master passwords and compromise of all cleartext passwords post-exploitation with a “living off the land” technique utilizing the Okta SWA (password manager) functionality.
Your ability to properly assess your risk is directly correlated to the breadth and depth of your intelligence.
For security teams seeking to protect against identity-based threats, they need to be able to answer basic questions like…

Authomize, the Identity Threat Detection and Response Platform, announced today the launch of the OpenITDR Framework Initiative.
Identity attacks are increasing and putting organizations’ data at risk. Look out for these 5 warning signs of an identity attack: stale accounts, user impersonation, lateral movement…

Despite their best intentions, organizations find themselves contending with all too common admin sprawl throughout their apps and environments, leaving them with far more admins than they can handle securely…
Discover the motives and behavior of cyber criminals and how to protect yourself with Authomize’s Identity Threat Detection and Response (ITDR) platform.

Okta’s source code was stolen in a breach of their GitHub repos, marking the 2nd significant attack on this critical IAM provider. Read how to secure your Okta with ITDR.

Earlier this month, the team over at security firm Kroll released its “Q3 Threat Landscape: Insider Threat the Trojan Horse of 2022” report on the rise in insider threat…
Authomize announced today that we are the Identity Threat Detection and Response (ITDR) Platform. If you missed our Press Release on the announcement, take a moment to check it out…

In response to the expanding threat surface facing identities, interoperability between identity and access management (IAM) and security operations is now understood to be a must for organizations in defending their cloud environments…

Following the new Gartner research report around Identity Threat Detection and Response (ITDR) we suggest 3 steps that help organizations get started with protecting their IAM layer from identity threats.
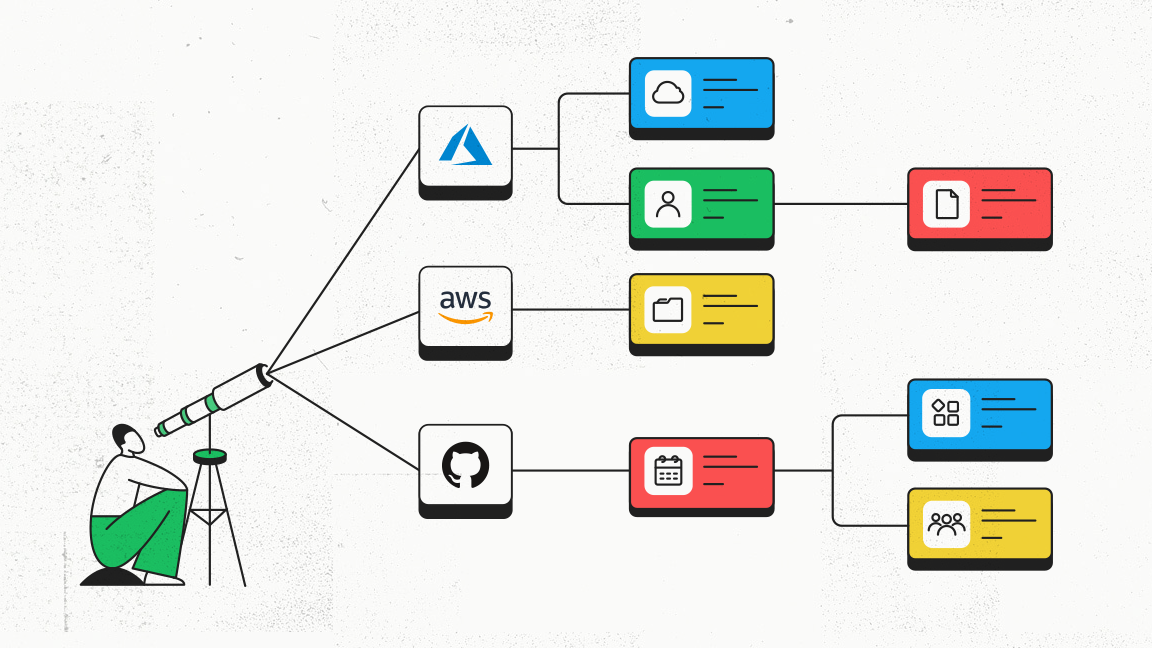
We here at Authomize have released an updated Access Explorer that gives security teams the highly detailed view of access to their assets that makes it easy to investigate and resolve incidents.

Organizations depend on their Identity Providers for managing their identities and access to their apps and services, using them as their trusted management solution for everything from Single Sign-On and Multi-Factor Authentication to directory services and provisioning access.

Authomize’s Security Research Lab has uncovered a set of inherent risks in the popular Identity Provider Okta that leave users exposed to potential compromise and exploitation..

Learn how Authomize's solution is changing the way companies are managing authorizations
Download