Importance of SOC audits to build customer confidence

Joseph Carson
System and Organization Controls (SOC) isn’t a prescribed framework like NIST 853, or ISO 27001, or a mandatory compliance requirement. Rather, it’s a reporting framework companies use to provide depth and transparency to third parties, demonstrating that controls have been defined for the products and services they deliver.
SOC reports are typically given to customers rather than to regulators so they can evaluate the risk of a purchase.
SOC certifications benefit SaaS companies, especially those that sell to the U.S. Federal government, companies in the European Union, and regulated industries. As such, SOC certification directly impacts revenue, as many customers prefer or will only work with vendors that have passed a SOC audit.
While the audience and purpose are different from the typical compliance process, a SOC evaluation can be just as time-consuming and intensive for IT and security teams who need to gather evidence to provide to SOC assessors.
First, let’s unravel the confusing terminology used for SOC assessments so you can determine the best types for your organization to pursue and see exactly what’s involved.
Understanding types of SOC audits
There are several types of SOC standards.
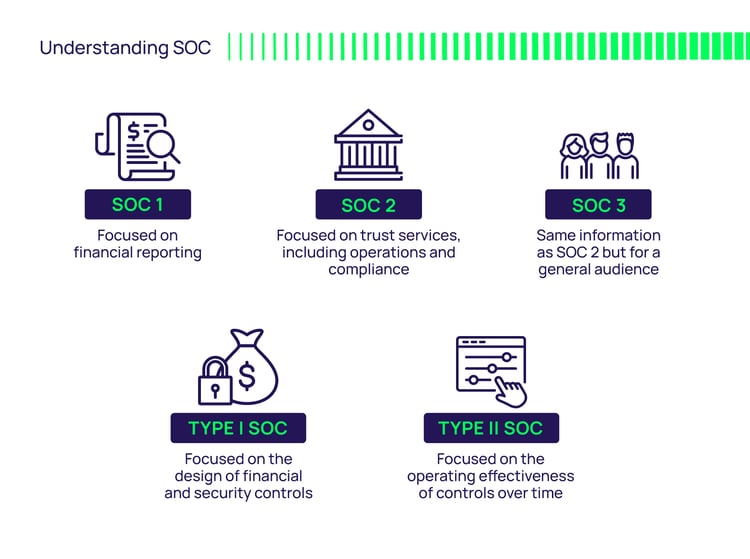
- SOC 1 is focused on financial reporting. SOC assessors are looking for financial controls that make sure the transaction cycle is complete and accurate so they can evaluate financial risk. It should demonstrate that logical access, change management, etc. are in place to match financial statement assertions.
- SOC 2 is focused on trust services, including operations and compliance. It’s devised to provide transparency around certain criteria related to security, confidentiality, availability, processing integrity, and privacy.
- SOC 3 is a variation of SOC 2. It contains the same information as SOC 2, but it's presented for a general audience rather than a technical one.
What’s the difference between Type II and Type II SOC reports?
It’s easy to confuse SOC 1 and SOC 2 standards with TYPE 1 and TYPE 2 reports. The SOC “types” have to do with the level of reporting, not the scope of information.
A Type I SOC report is a design-based report. The report will need to cover the design of your financial and security controls. You’ll need to include information to show how those controls meet criteria and objectives, and you’ll be judged on the accuracy and completeness of the description.
A Type II SOC report demonstrates the operating effectiveness of controls over time. It describes how a company’s control environment operated over its audit period (typically not less than six months). This is extremely important to help third-party organizations measure the full maturity of a control to establish what their residual risk is. They don’t want to see any gaps in coverage.
What to expect during a SOC audit
During a SOC audit, you’ll be expected to answer a lengthy security questionnaire and collect evidence of your controls. In this way, SOC audits are very similar to compliance reviews and cybersecurity insurance assessments.
For example, all those evaluations will ask about PAM best practices such as password management, access controls, Multi-Factor Authentication (MFA), and similar cybersecurity policies and controls that reduce the risk of cyberattacks. The good news is that you can likely use much the same information for your SOC audit as your regulatory and insurance reviews.
Once you’ve completed those steps, a SOC evaluator will review your answers and follow up to ensure the depth and detail of your answers. Finally, a report is generated that represents your SOC certification. You can then provide that SOC report to any customer or partner who asks.
How to prepare for a SOC audit: people, process, and technology
People
For a SOC audit to succeed, it’s essential to involve the internal teams. The executive team will be your sponsors, and they’ll need to provide the time and resources to be able to fulfill the SOC assessment requirements. Beyond the executive team, you’ll need involvement from technology, operations, legal, privacy, data governance, finance, HR, and more.
Process
At the start of the SOC process, the folks conducting a SOC audit need to determine which areas of the product or service are most relevant for their service level commitments. Any areas are considered a Trust Services Point of focus and will need to have demonstrated evidence of proper controls to ensure the SLA.
Steve Ursillo, who was on the Working Group to develop SOC points of focus, said, “What that does is allow for a reporting framework like SOC 2 to take something like security and all those points of focus and map those to other criteria. You could do a SOC 2 in which your controls could map to the points of focus and also to ISO. They could also map to the NIST cybersecurity framework. If you’re operating in the healthcare space on HIPAA, then your focus areas should include the controls designed to do that. The list is endless, depending on what those commitments are.”
You can hear more from Ursillo in our podcast "Securing Compliance: Expert Insights with Steven Ursillo" below:
To be ready for a SOC assessment, it’s," helpful to conduct some dry runs, both internally and with an experienced third party who has conducted numerous SOC audits. You’ll want to choose a SOC auditor who has experience with your type of products, SLAs, compliance requirements, and IT environment and understands the latest attestation standards. AICPA provides authoritative guides to help you and your SOC auditors understand SOC requirements.
Technology
How long a SOC audit will take will depend heavily on how well your controls are designed, maintained, and documented. Steve warns, “If it's a manual and very human process and information is hidden within documents and data, that's going to be a very difficult place to get started.”
An automated system for control reporting speeds up the process. For example, a Privileged Access Management (PAM) solution can provide reports demonstrating the effectiveness of privileged access controls, including audits of privileged user behavior.
What happens if you don’t pass a SOC audit?
Let’s say you don’t achieve SOC certification. You can keep working towards that goal. A SOC analysis helps you identify any gaps in your security and compliance posture that increase your risk. Based on the findings of your SOC assessment, you can develop your cyber program roadmap, make the case for additional investment, and prioritize your resources.
Next steps to SOC success
As our CISO here at Delinea likes to say, “Comply once, apply many.”
Map your cyber controls, including Privileged Access Management (PAM), to industry standards and best practice frameworks like NIST and ISO. By building your cyber program on top of those frameworks and automatically gathering the evidence you need to demonstrate compliance, you’ll save time in your SOC audit process and be more confident of a successful result.

Meet NIST SP 800-171 Requirements



