9 PAM best practices to prevent ransomware and mitigate its impact on healthcare organizations

Tony Goulding
The ransomware attack on Change Healthcare sent shockwaves through the healthcare industry. UnitedHealthcare reportedly paid $22 million to ransomware group AlphV/BlackCat to recover operations.
This isn’t an isolated incident. Healthcare organizations have become top targets of ransomware gangs in recent years.
The impact of ransomware in the healthcare sector is significant. Attacks have cost the United States $78 billion in downtime since 2016, according to Compirtech. In addition to financial costs, ransomware attacks on healthcare can be life-threatening if they prevent access to medical treatment.
Other notable incidents involving healthcare include the ransomware attack that brought down the Irish Health Service in 2021, which initially cost around 100 million euros, potentially rising to 500 million euros to implement significant cybersecurity improvements. In another high-profile case, patients of a Vermont Medical Center were left without access to life-saving cancer treatments when the hospital fell victim to a ransomware attack in 2020. Setbacks and financial losses from this attack continued well past the original event.
Our thoughts are with the security professionals responding to ransomware attacks like these, and we hope that lessons learned from these incidents can be shared and implemented to prevent future attacks.
In this blog, you’ll learn best practices to help healthcare organizations survive ransomware attacks, reduce impact, and maintain the trust of patients and medical practitioners.
Ransomware trends healthcare organizations need to know
In a traditional ransomware event, malware encrypts files on a device, rendering systems that rely on them unusable.
As Delinea covered in our recent research on ransomware, attack strategies evolved in the past year, adopting a stronger focus on data exfiltration. Unlike the destructive encryption payloads of the past, cybercriminals now strategically extract sensitive data, allowing them to operate without raising alarms or disrupting victims' business operations. Many organizations discover attacks only after the ransomware has been activated.
Ransomware disrupts operations, impacting patients and medical staff. The damage is more extensive if data encryption is paired with data theft, resulting in a double-extortion scenario that exacerbates the distress, prolongs the forensic investigation and negotiation process, and delays the resumption of operations. Whether or not you choose to pay the ransom, recovery is rarely straightforward, quick, or comprehensive, for several reasons:
- Decryption keys may not work. The initial encryption may be flawed, resulting in failed decryption.
- You may have several backup mechanisms with different tools, schedules, and restoration processes. Some systems may depend on the availability of others before they can be fully operational again.
Backup contamination is a big concern. Restoring your latest backups can potentially re-introduce the ransomware, allowing the attacker to regain access and attempt further extortion. Unfortunately, this may require you to restore stale data and manually re-create content. The bigger the time gap, the more effort it takes to manually restore.
Some reports tell us that more victims are declining to pay extortionists. As a result, many ransomware groups are currently favoring a quality versus quantity approach, called “Big Game Hunting,” in which they focus on larger targets with more money and more to lose.
Healthcare providers fit the bill.
These days, ransomware groups don't have to be experts in all required tactics and techniques to achieve their goals.
- Ransomware-as-a-Service (RaaS) platforms, tools, and services can help relatively unskilled actors launch sophisticated attacks. Services like initial access brokers (IAB) can be bought or leased. Affiliate programs can offer ransomware tools and services in exchange for a cut of the profits.
- AI tools can streamline and simplify ransomware tactics such as surveillance, social engineering, and analysis of harvested data. A report from the National Cyber Security Centre in the United Kingdom warns of increased attack attempts and complexity as cybercriminals increase their use of available AI tools.
What's the difference between ransomware prevention and ransomware mitigation?
Security and IT leaders must be proactive as well as responsive, employing a balanced approach to ransomware prevention and mitigation.
- Ransomware prevention is about stopping attacks before they happen through good security hygiene. Proactive security activities include keeping systems patched and updated, restricting user access, blocking suspicious emails/attachments, training employees on threats, and maintaining good backups. Focusing on prevention reduces the likelihood that attacks will succeed and breach systems in the first place.
- Ransomware mitigation is about responding quickly and effectively to contain an attack once it’s underway to limit its impact. This includes having incident response plans, isolating infected systems, restoring from recent backups, leveraging cyber insurance if needed for recovery, and more. Having good mitigation ensures that even if preventative controls fail, the organization can still recover operations with minimal disruption.
In the ongoing battle against ransomware, you need a robust and multi-layered strategy.
PAM is a best practice for both ransomware prevention and mitigation
In this next section, you’ll learn nine strategies to incorporate PAM into your anti-ransomware program. With PAM, you can proactively stop ransomware attackers from gaining access to your environment in the first place. Plus, if stealthy and sophisticated attackers do find a way in through advanced techniques or human error, PAM can help you detect, contain, and mitigate the impact.
1. Discover and manage privileged credentials
Every significant ransomware attack leverages compromised privileged credentials to execute tactics such as escalating privilege, moving laterally, and exfiltrating or encrypting data. PAM solutions can mitigate these risks by vaulting and rotating shared privileged credentials, enforcing least privilege, using AI to detect anomalous behavior, enforcing MFA at depth, temporarily elevating permissions, and protecting access to workstations and servers.
Continuous discovery of users, roles, permissions, and systems on-premise and in the cloud (via Cloud Identity Entitlement Management or CIEM) provides visibility, and entitlement certification campaigns contribute to a strong identity governance posture. Continuous discovery is essential to quickly identify shadow IT and rogue systems and accounts created by threat actors. These must be identified, investigated, and, if necessary, terminated.
2. Use protection strategies based on zero trust
PAM has become a business imperative and a crucial element of the zero trust model. Many reports highlight zero trust benefits and increased adoption of solutions that support zero trust principles. Organizations such as the National Institute of Standards and Technology (NIST) in the United States provide recommendations and guidelines for using zero trust to enhance security posture. An example is the NIST Zero Trust Architecture.
Other organizations, such as IBM, discuss why zero trust should guide your security strategy and how PAM is a foundation for zero trust. Foundational to zero trust are PAM capabilities such as least privilege, just-in-time privilege elevation, and MFA to enforce the concept that no user or system is trusted by default, and every request should be verified as though it originates from an open network.
3. Implement the Principle of Least Privilege (PoLP)
Identity security relies on reducing standing privileges to the absolute minimum to reduce the attack surface. If privileged accounts are abundant, shared routinely, and poorly managed, all the risks outlined earlier, such as unsanctioned lateral movement, increase. PoLP is a foundational tenet of many best practices (such as zero trust), security frameworks (such as NIST Cybersecurity Framework or CSF), and HIPAA, PCI DSS, FISMA, and GDPR regulations. Thus, a PAM solution designed around a least privilege access control model helps ensure you provision user accounts, applications, and services only those privileges that are essential to perform its intended function.
Least privilege access controls can mitigate ransomware risks across several fronts. They can be preventive, presenting a smaller attack surface that gives attackers less opportunity. They can help contain a threat actor if they get a foothold on a workstation or server in several ways, such as preventing privilege escalation and vertical or lateral movement, demanding proof of identity via MFA, and requiring explicit just-in-time access requests. They can also be detective, leveraging AI to analyze session recordings and looking for abnormal behavior that might be an indicator of compromise (IOC.)
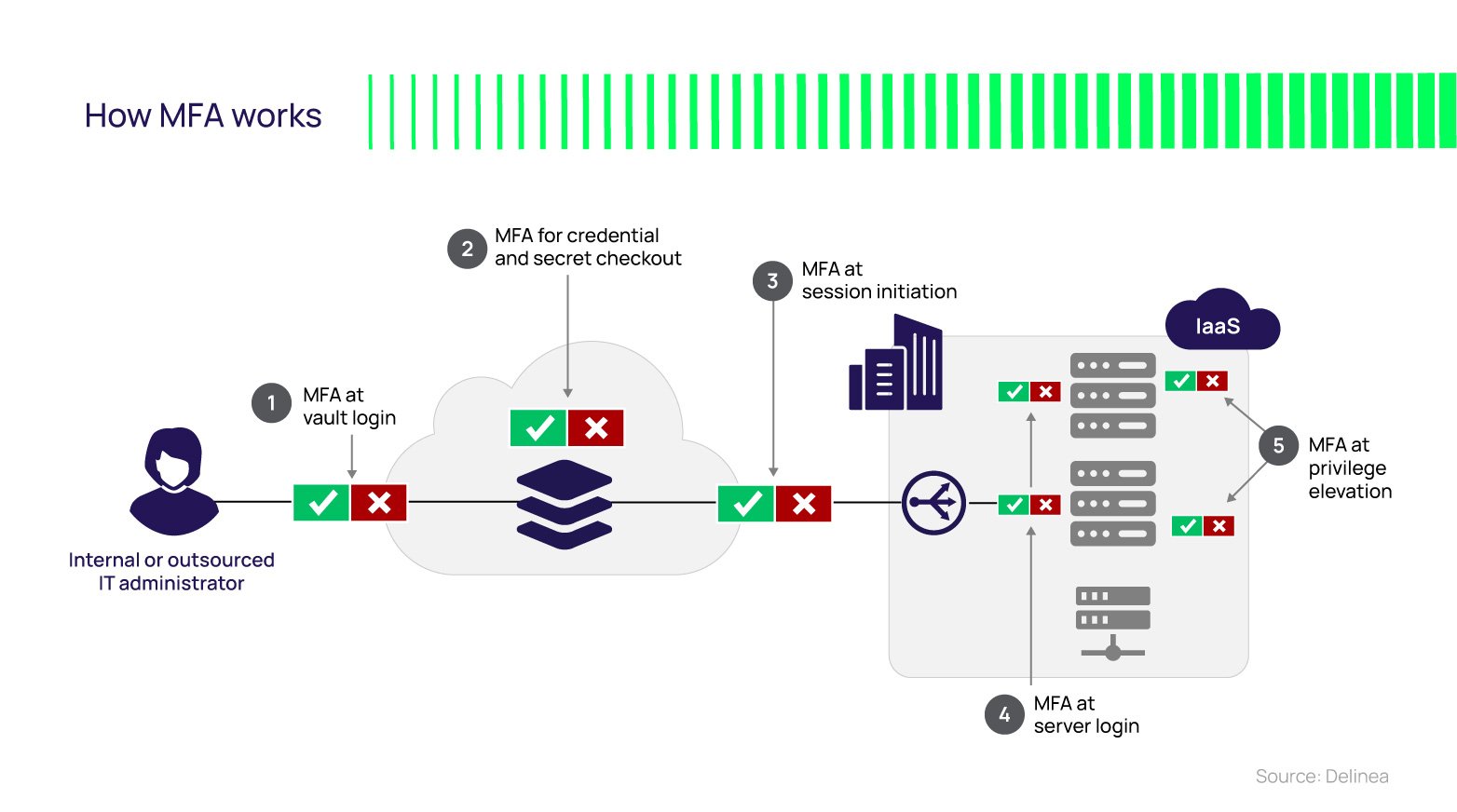
4. Enforce Multi-Factor Authentication (MFA)
Implement Multi-factor authentication (MFA), especially for remote vendor access to sensitive systems, to make unauthorized access more difficult. Expand MFA coverage to all places where you control administrative access, per the diagram above. Whether you bring your own MFA or leverage authenticators built-in to the PAM solution, leverage MFA policies in PAM so you can centrally manage MFA at depth and control which second factors are appropriate based on the user, resource, context, and risk score.
5. Enhance remote access security
Being resilient should not only focus on access to resources by employees inside your networks. Many attacks originate externally, for example, through compromised third-party vendors or supply-chain partners. Although you have less control over third parties' security hygiene, with secure remote access, PAM can help make such ingress points more resilient. Examples include the use of SAML-based identity federation and VPN-less browser-based login.
SAML single sign-on provides users with a better experience and is more secure than traditional IDs and passwords. SAML assertions can be encrypted to prevent third-party tampering. SAML-based partnerships make it easier for the relying party to manage third-party access and quickly remove it when the partnership terminates. SAML can also support a zero trust strategy, enforcing MFA policies and conditional access.
While VPN usage exploded during COVID-19 to support an overnight remote workforce, its usability limitations and security risks are well understood. Enterprises moving to the cloud risk their Virtual Private Cloud's (VPC) privacy by requiring VPN access through firewall exceptions. Browser-based secure remote access mitigates these risks and offers users and IT convenience by not relying on dedicated clients and servers. It provides a "clean source" by not connecting remote computers to the target network, avoiding the potential spread of viruses and malware. As a SaaS, secure remote access is available from anywhere, via a browser, without chaining the user to their enterprise laptop.
6. Audit all privileged activity
Logging and reporting remain table stakes for any access control solution. They help your incident response team investigate ransomware indicators of compromise. Modern PAM solutions will augment this with additional capabilities. Session recordings will visually capture privileged activity. This can accelerate incident response activities where time is critical. Ensure session recording is performed at the host operating system level to ensure visibility across the entire infrastructure. Also, PAM can capture shell and process-level metadata for forensic quality details such as commands entered and shell expansions (to reveal attempts at obfuscation, hiding privileged commands behind aliases or inside shell scripts.)
7. Offline backups of critical data
So far, we've focused on ways to combat ransomware attacks to break the attack chain at several points. However, you must also have a robust incident response process if an attack succeeds.
Although backup and restore are not strictly PAM functions, PAM can help ensure access to systems and data when you restore your backups. If you made a backup before password changes, restored systems and accounts will have the old passwords, resulting in failed access. PAM solutions can maintain a history of password changes so the old password is always available.
It's also crucial to ensure your backup and restore procedures incorporate your PAM system's data to ensure password history is available. You can introduce more resilience by subscribing to a PAM-as-a-Service instead of an on-premise deployment.
Also, you can preserve password history with a "resilient secrets" capability that replicates Secret data to a separate instance either on-premise or in the cloud, with automated synching across instances. Finally, a PAM solution with a "heartbeat" function that regularly tests vaulted credentials against the target system ensures they're valid to help avoid situations where a threat actor changes an account password.
8. Use AI to detect anomalous activity
Adversaries will leverage AI, so why not defenders? Use AI to scan activity events, looking for abnormal behavior that would otherwise go unnoticed.
Early detection is a critical component of your defense strategy. It can help prevent an incident from becoming a full-blown breach. It can help detect attempts at persistence, where the threat actors work to maintain long-term access to your systems, even in the face of disruptions such as system restarts or changed credentials. As discussed earlier, this can reduce the gap between current data and the last known clean data in your backups.
9. Quantum-safe cryptography
PAM can play a role in helping defend against post-Quantum encryption and prevent Store Now, Decrypt Later (SNDL) attacks, in which attackers harvest your encrypted data for a future time when they can easily decrypt it. While this might not be an immediate concern for many, it's good to have your eye on that ball in your planning.
Looking for more ransomware best practices for healthcare?
Click here to see how PAM is foundational to healthcare IT security

6-in-1 Toolkit for Ransomware Defense



