Remote Desktop Protocol (RDP)
What is Remote Desktop Protocol?
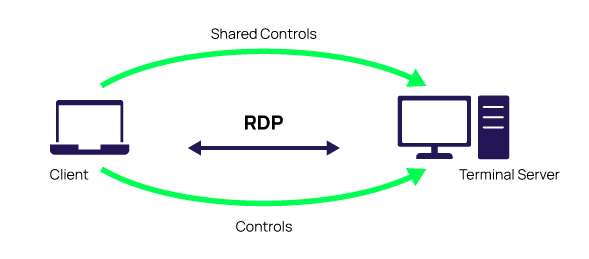
RDP stands for Remote Desktop Protocol. Remote Desktop Protocol enables a communication tunnel between the Terminal Server and the Terminal Server Client. It is critical in today’s digital business world of remote staff as it allows the organization to support remote users efficiently.
Read on to get a basic understanding of RDP—what it is, how it works, RDP best practices, and a few more Remote Desktop Protocol basics. This is not a comprehensive explanation of RDP and its architecture but rather an introduction to RDP along with some helpful details on RDP alternatives, RDP security, and more.
Let’s start with the definition. Remote Desktop Protocol is a Microsoft protocol that provides users with a graphical interface to connect to another computer over a network connection. In essence, it allows remote users to use Windows on a device in another location like they were sitting right in front of it.
Example of RDP real-world use: You are having issues with your work computer and reach out to your company network admin (or Help desk). They will use RDP connections to diagnose the problem and take over to make adjustments on your local computer like they were in your office, with your mouse.
To use RDP, you will need two fundamental things. First, an RDP server, which is a Windows PC you are connecting to, or a server. Either way, it will be the one you will control. The second essential thing you will need is an RDP client, your device with an RDP client app installed. You will use this device to control the Windows PC or server with your mouse and keyboard.
Before we move on, let’s quickly differentiate the meaning of RDP from VPN. Some people think these technologies are similar—they are not.
- Virtual Private Network (VPN) allows connectivity to a remote network
- RDP enables connectivity to specific remote resources, usually a physical computer.
Who uses RDP?
Network administrators use remote Desktop Protocols to troubleshoot, diagnose and fix problems that individual users encounter. RDP allows remote access to the particular user’s physical desktop computers.
Individual business users can also use an RDP connection to access their computers remotely. They will need to have the Remote Desktop Gateway configured and installed to use it.
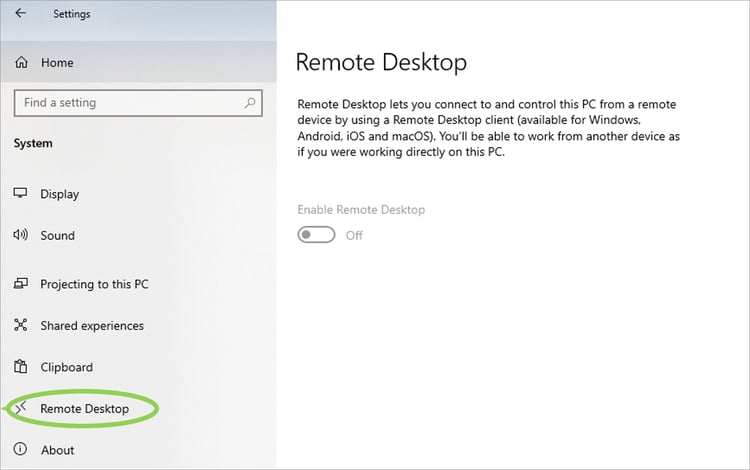
How do I enable RDP?
RDP connections are easy to find and access on your computer. Remote Desktop Protocol allows remote capabilities over network connections for Windows-based applications running on a server. To allow access to your PC from a remote device, you can find RDP options under Settings.
When you enable RDP, be aware that you are giving anyone in the administrator’s group and select users access to your computer, so choose wisely.
Remote Desktop Protocols Best Practices
Over the last few years, the use of remote desktop protocols has expanded exponentially as a quick fix to the number of workers needing access to systems from home or other locations outside the network. Although there are numerous security concerns with remote desktop services to enable access, it is still widely used.
- Restrict access to those with Network Level Authentication (NLA). This ensures that users must authenticate before they can connect to your computer.
- Change your default port—if you have access!
- Ensure that every account on your PC has a strong password and make MFA mandatory when you enable remote access protocols—an essential RDP security best practice.
- Enable automatic Microsoft updates on both Client and server software and prioritize RDP patches.
- Use account lockout policies. This makes sure that a bad actor cannot use brute-force attacks.
- Least privilege—not only for Privileged Access Management PAM these days. Enable least standing privilege with limited permissions, so only employees who need remote access have RDP access.
- Monitor, monitor, and monitor again. Know who has access and how they use it. This allows you to identify anomalies and failed login attempts.
- Don’t allow RDP to be open to the internet and scan the network to identify RDP instances still open to the internet—AND fix them.
The key to RDP security best practices is to ensure the external security protocol handshake is secure before transmitting anything. It is recommended to route RDP connections through your secure PAM solution. Routing each RDP connection through your PAM solution adds another layer of encryption and restricts lateral movement from a bad actor. This also allows all sessions to be monitored and recorded.
Try Our Free IT Tools
What are the advantages and disadvantages of RDP?
In using RDP, pros and cons are dictated by whom you ask, but here are a few that most agree on.
Remote Desktop Protocol Advantages:
- RDP allows flexible access
- RDP setup is flexible and cost-effective
- It does not require the use of a VPN
- It enables workers at companies with legacy on-premise IT infrastructure to work remotely
- Remote Desktop Protocols allow for improved efficiency and collaboration
Remote Desktop Protocol Disadvantages:
- RDP security issues
- RDP data liabilities
- Can be open to open internet connections, increasing vulnerability
- Hardware issues—may still need onsite work
- The Windows version impacts vulnerabilities, and updates must be current at all times
RDP alternatives
RDP alternatives are easy to find, and each has pros and cons. If you feel you need an alternative to your RDP, research to find the alternative that works for your environment and culture and integrates with your PAM solution. With the transition to the cloud, explore your PAM solution to see if they offer a secure remote access service you can utilize.
Are there any security fixes for RDP?
There are security risks associated with using RDP, but there are two types of security built into RDP.
RDP standard security employs RSA’s RC4 encryption algorithm to protect data. This assigns random values between the client and server during the initial connection while machines are in the Basic Exchange phase. RDP’s standard security protects data being transmitted from unauthorized use.
RDP enhanced security, encryption, decryption, and integrity checks can be outsourced to external security protocols such as: Credential Security Support Provider (CredSSP), Transport Layer Security Protocol (TLS), or Network Level Authentication (NLA)
Microsoft provides security patches as needed making RDP more secure. Microsoft has options to help users and admins follow best practices.
RDP attacks are a favorite for bad actors. They focus on known vulnerabilities before Microsoft can release the patch, and you can update. Although brute-force attacks are less effective, they are still used, which is why account lockout policies are critical.
Remote Desktop Services is an umbrella term that allows you to expand your environment beyond a local network.
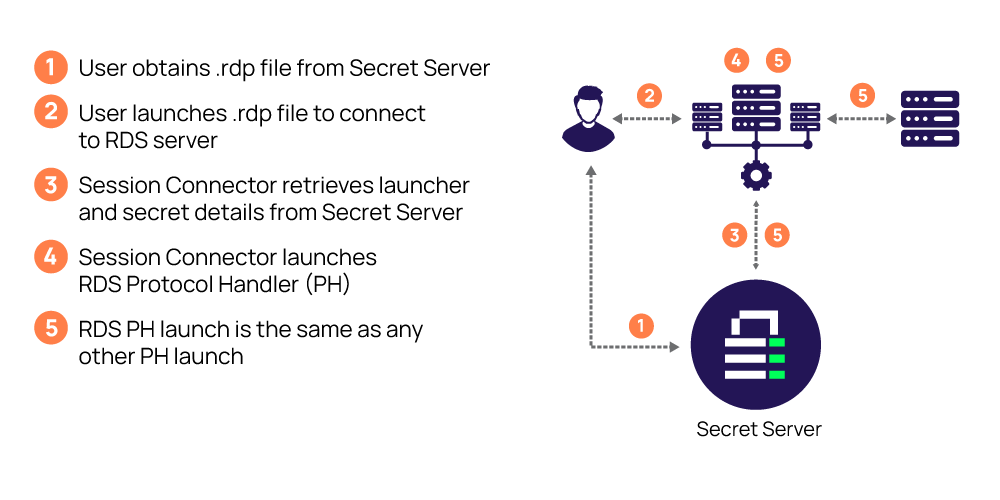
Remote Desktop Protocol is not complex to enable or use and comes with its own advantages, disadvantages, and challenges. Use RDP best practices and layers of security to protect your assets and route through your Privileged Access Management tool when possible.
More RDP Resources:
Blog Posts
RDP Security: What is RDP and how do you secure it?
SSH proxies vs. jump hosts—securing RDP

FREE EBOOK
Definitive Guide to Endpoint Privilege Management
