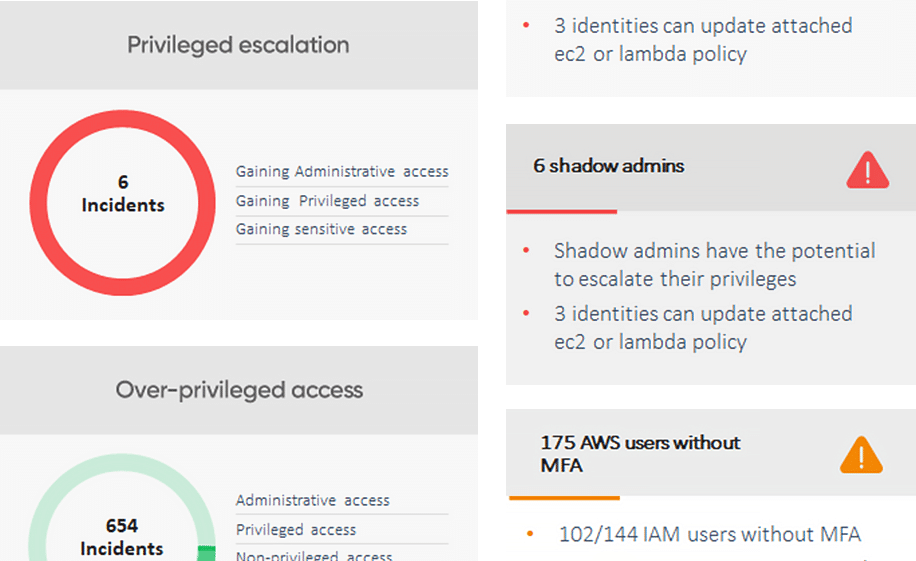
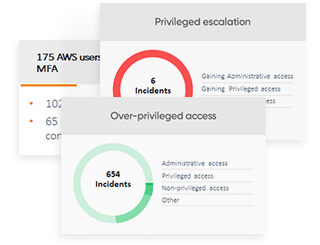
Enhance incident investigation, prioritization and correlation with unmatched visibility of identities, assets, access privileges, and activities from a single pane of glass.
- Comprehensive, unified visibility across IaaS, SaaS and IAM
- Granular visibility into every file, VM, and code repository
- Proprietary rich context and ML-generated insights (SmartGroups)